Mobile Personas Help Solve BYOD Issues
The bring-your-own-device (BYOD) trend continues to be a growing trend for businesses. In fact, according to Gartner, 38 percent of companies expect to stop providing devices to workers by 2016, and by 2017 half of all businesses will require employees to provide their own mobile devices. Researchers have estimated that there will be more than 1 billion employee-owned smartphones and tablets in use in enterprise business by 2018. As a result of the rapid influx of employee-owned mobile devices, more than half of North American and European companies are developing a BYOD policy, according to Forrester Research.
Benefits of BYOD
Allowing your company’s employees to use their personal smartphones and tablets for work enables small and medium businesses, as well as large enterprises, to leverage technologies that otherwise would be too expensive to implement on existing budgets. When it comes to the benefits of BYOD, an enterprise could spend $500,000 to buy and support 1,000 tablets, or it could spend the same amount to support 2,745 tablets that its employees own and bring to work. So says the research firm Gartner, which predicts that those kinds of savings are a major reason why in 2016, 40 percent of organizations will have stopped providing their employees with smartphones and tablets.
And cost savings is not the only benefit. A BYOD program can benefit your organization with increased worker satisfaction, more up-to-date devices, enhanced productivity, and possibly increased engagement in the workplace and after hours. Unfortunately, the numerous benefits also come with a few caveats due to clashes between company security policies, privacy laws, and employee privacy concerns.
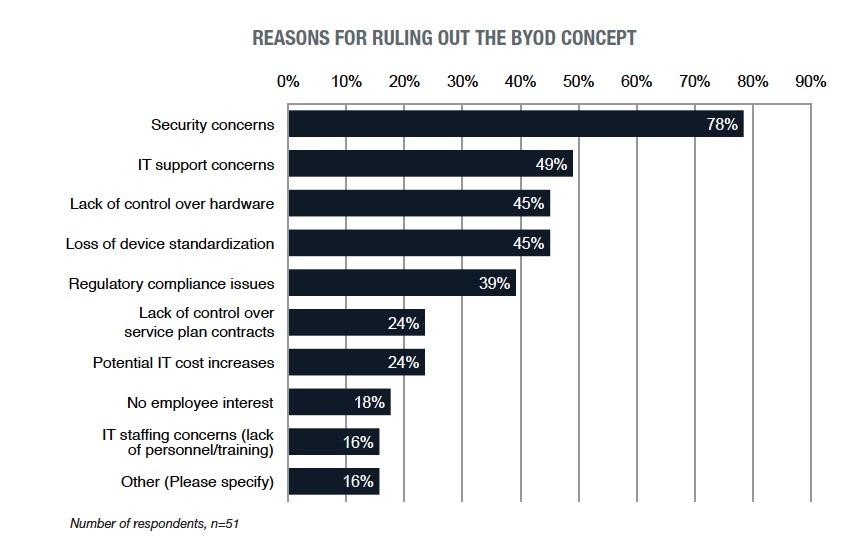
Why Organizations to Hesitate Adopt BYOD
So why is it that 60 percent of organizations still provide mobile devices? It’s mostly for security reasons. A Tech Pro Research survey, found that enterprise IT departments said security and control concerns were major reasons why they had not implemented their own BYOD policy:
BYOD security concerns were mentioned by 78 percent of respondents. After security, IT support concerns, lack of hardware control, and loss of a standard device were the next most frequently mentioned reasons.
According to Gartner, the 40 percent of organizations that have instituted BYOD programs aren’t ignoring these concerns. Instead, many have deployed enterprise mobility management (EMM) platforms, which enable them to remotely enforce company policies, ensure regulatory compliance, and manage and erase company data on stolen or lost smartphones and tablets. These EMM capabilities can be applied to both employee-owned and company-owned devices, allowing organizations the flexibility to implement a BYOD program at their own pace and scale.
BYOD Device Controls
One of BYOD’s overarching challenges is control: control of data, and control over whose data is whose. For example, employees are frequently concerned that the EMM platform will archive their personal data such as photos, messages, and other files as part of their employer’s effort to comply with archiving and compliance laws such as Dodd-Frank, which requires financial services firms to retain business communication including text messages, social media content, instant messages, emails and voice call logs. This concern often causes employees to do one of two things: they refuse to participate in BYOD programs, which undermines the bottom-line and productivity benefits for their company. Or, they agree to participate in the BYOD, but attempt to circumvent the EMM system in ways that create security risks for the company, like storing company information in third-party cloud services.
“Dual-Persona” Security & Archiving
Wouldn’t it be great if your company could implement a solution that would resolve many of these BYOD issues for you and your employees? When your company implements a persona-based system, it will all be possible.
This type of mobile security and archiving solution, needs to support both iOS and Android, and a “persona” architecture, which separates business and personal calls and data. This design enables organizations to apply policies—such as data erasure and archiving—only to the business persona data, as opposed to solutions that archive at the carrier level, or by using device syncing, where all communication data from the device is archived. Plus, carrier-level archiving solutions do nothing to address iMessage, meaning that an organization will have no oversight on employee communication done on iPhones with iMessage. With dual-persona, an organization can advise against the use of iMessage for business communication, while using the business persona for all business communications allowing full oversight.
A dual-persona solution greatly increases the likelihood that employees will feel comfortable using their personal device at work, which means the business will benefit more from BYOD as a result of increased participation. And with dual-persona, organizations benefit from faster, more authentic forensics, because archives aren’t filled with personal data.
Persona-based mobile security integrated with EMM is an ideal way for companies, government agencies, and other organizations to reap BYOD’s benefits without tradeoffs that they and their employees can’t accept. In fact, the combination is one more reason why you’ll see even more organizations implementing BYOD this year.
Next Steps:
- Learn more about the business case to archive mobile, text, and voice data, and look at the best practices for archiving and compliance by downloading our FREE white paper, “Adopting a Mobile-First BYOD Strategy”
- Check back for our upcoming white paper, “Mobile Tools for Risk Mitigation and Compliance”
- Read the blog post “Top 10 Bring Your Own Device (BYOD) Business Concerns”
- Learn about the CellTrust solution for “dual persona,” CellTrust SecureLine
Learn about the GWAVA solution for archiving mobile communication data with CellTrust, along with all other electronic communication data, by using Retain Mobile